


A security incident report is a vital tool for documenting security-related incidents. Multiple industries will utilize a security incident report from cyber attacks to break-ins as part of their incident recording toolset. However, it is vital to understand how a robust solution can work for everyone, from IT managers to security firm supervisors overseeing officers patrolling field locations.
Observing that both the IT industry and security (as well as law enforcement) will utilize a security incident report regularly, we’ve chosen to focus on these sectors. Surprisingly as it may seem, the methodology for reporting security incidents in either vertical is quite similar. That is, despite what many might think.
We’ll explore how a robust tool like our Security Incident Report Template that you can download on this page will work with IT or security sector security incidents. Furthermore, we’ll look at the downloadable template and provide a quick brief on its intended use. Lastly, we’ll give you some great ideas about how you can streamline your security reporting methodology, so stick around. Let’s get into it.
Table of Contents
Our Security Incident Report Template is intended for use by:
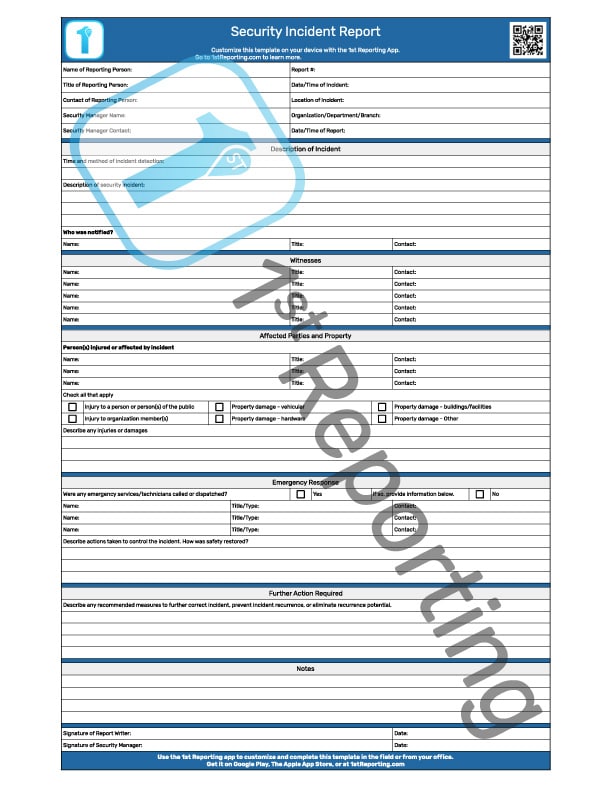
The Security Incident Report we’re providing you with is a complete report on a single page but has several segments dividing the observations and data for easy reference. These segments include:
Following, you will find a very brief description of each that you can use to train your team members on the intended use of the template.
As you are no doubt aware, security incidents require the utmost care and caution. Not only do these incidents need team members to react in a proper fashion, but also to follow what are sometimes lifesaving procedures. These processes are often incredulously scrutinized after the fact.
Considering this scrutiny, we’ve included many critical data fields for completion at the beginning of the template. This data will help you to keep your incidents organized and tracked appropriately.
Again, somewhat obviously required, we’ve included the primary section where your team will note their observations of the incident in terms of incident description. They must note the time and method of incident detection (highly appropriate for cyber-related security incidents) and a description of the security incident (or breach).
Following the description is a short set of data fields where the reporter may note the person, their title, and contact information of whom was contacted due to the incident.
Often security incidents will draw a crowd. It is imperative to note the names and contact information of each witness. You should collect witness statements on separate forms and attach them to this document due to the potential length of witness statement form requirements.
Security incidents often affect people, property, or even entire companies in a negative way. It is best to record and document any person who is directly affected by the incident. It would seem to be obvious in the case where personal injury is involved. However, some situations might seem more subtle, and the affected person or persons might actually be overlooked. Therefore, teams need to consider all those involved when documenting the incident properly.
Any security incident, whether digital or physical in nature, will require a swift and strategic response. The primary goal is to remove any danger, treat any injured parties, and perform further actions to prevent an incident from recurrence.
This section of the Security Incident Report intends to provide an area where the incident reporting personnel might note their actions and the actions of others to remove the hazard.
As mentioned, further actions are often required after the initial incident mitigation occurs. Depending on your industry sector, it could mean a software update or bolstering facility security. Either way, you’ll find that including further actions to mitigate and prevent further security incidents is vital to a robust and successful incident reporting regiment.
Providing your team members with an area to compile further notes and observations is often critical for a proper documentation process. Therefore, you will find that we’ve included the section near the end of the document.
Lastly, on the document, you will find the sign-off. The sign-off includes data fields for a signature from the report writing team member and also that of the site security supervisor or manager. This double sign-off concept is critical to the operation of a healthy safety and security reporting system.

In case you aren’t familiar with security incident reporting, we’ve got some handy tips to help you keep your team on track to perform in the case of a security incident or emergency. Here’s a list of tips to help you manage security incidents and their reporting at your organization.
We’re pleased if you find our Security Incident Report Template useful. However, we have also provided an even greater solution that will work for all your reporting needs. We invite you to try the 1st Reporting app – a mobile form automation application that will drive your reporting process into the future of reporting today.
Digital reporting might seem different if you’re used to the old paper and pen treatment. However, just think of how some of these following benefits could help your organization.
Customizable Forms – Create forms specific to your organization’s needs. Customization is the name of the game here with a form builder that you just won’t get using paper forms.
Automated Workflows – Create automated workflows that easily change the form based on the responses provided. Utilize automation to offer a malleable form concept that can adapt as you see fit.
Customizable Notifications – Remember how we were talking about notifying a manager or someone of authority when an incident occurs? With customizable notifications, you can automate the process by having a custom notification sent to a specific individual upon report completion. Again we see how technology can save time and money by implementing automation into manual processes to increase efficiency.
Cloud-Based Storage – Retrieval of reports has never been easier. No more fiddling around in old creeky filing cabinets. And no more trusting someone filed something in the right place. You can retrieve documents and reports in seconds from a digital platform as robust and secure as 1st Reporting.
These are a few benefits you’ll find using 1st Reporting. So why wait? Try 1st Reporting for free and see what you think. We think you’re going to love it.